Social auth configuration
Note: This is a paid feature available for Enterprise clients.
You can now easily set up authentication with popular social services, which opens doors to such benefits as:
- Convenience: you can use the existing social service credentials to sign in to CVAT.
- Time-saving: with just two clicks, you can sign in without the hassle of typing in сredentials, saving time and effort.
- Security: social auth service providers have high-level security measures in place to protect your accounts.
Currently, we offer three options:
With more to come soon. Stay tuned!
Authentication with Google
To enable authentication, do the following:
-
Log in to the Google Cloud console
-
Create a project, and go to APIs & Services
-
On the left menu, select OAuth consent, then select User type (Internal or External), and click Create.
-
On the OAuth consent screen fill all required fields, and click Save and Continue.
-
On the Scopes screen, click Add or remove scopes and select
auth/userinfo.email,auth/userinfo.profile, andopenid. Click Update, and Save and Continue.
For more information, see Configure Auth Consent. -
On the left menu, click Credentials, on the top menu click + Create credentials, and select OAuth client ID.
-
From the Application Type select Web application and configure: Application name, Authorized JavaScript origins, Authorized redirect URIs.
For example, if you plan to deploy CVAT instance onhttps://localhost:8080, addhttps://localhost:8080to authorized JS origins andhttps://localhost:8080/api/auth/social/goolge/login/callback/to redirect URIs. -
Create configuration file in CVAT:
- Create the
auth_config.ymlfile with the following content:
--- social_account: enabled: true google: client_id: <some_client_id> client_secret: <some_client_secret>- Set
AUTH_CONFIG_PATH="<path_to_auth_config>environment variable.
- Create the
-
In a terminal, run the following command:
docker compose -f docker-compose.yml -f docker-compose.dev.yml -f docker-compose.override.yml up -d --build
Authentication with GitHub
There are 2 basic steps to enable GitHub account authentication.
-
Open the GitHub settings page.
-
On the left menu, click <> Developer settings > OAuth Apps > Register new application.
For more information, see Creating an OAuth App -
Fill in the name field, set the homepage URL (for example:
https://localhost:8080), and authentication callback URL (for example:https://localhost:8080/api/auth/social/github/login/callback/). -
Create configuration file in CVAT:
- Create the
auth_config.ymlfile with the following content:
--- social_account: enabled: true github: client_id: <some_client_id> client_secret: <some_client_secret>- Set
AUTH_CONFIG_PATH="<path_to_auth_config>environment variable.
- Create the
-
In a terminal, run the following command:
docker compose -f docker-compose.yml -f docker-compose.dev.yml -f docker-compose.override.yml up -d --build
Note: You can also configure GitHub App, but don’t forget to add required permissions.
In the Permission > Account permissions > Email addresses must be set to read-only.
Authentication with Amazon Cognito
To enable authentication with Amazon Cognito for your CVAT instance, follow these steps:
- Create an Amazon Cognito pool (Optional)
- Set up a new app client
- Configure social authentication in CVAT
Now, let’s dive deeper into how to accomplish these steps.
Amazon Cognito pool creation
This step is optional and should only be performed if a user pool has not already been created. To create a user pool, follow these instructions:
- Go to the AWS Management Console
- Locate
Cognitoin the list of services - Click
Create user pool - Fill in the required fields
App client creation
To create a new app client, follow these steps:
- Go to the details page of the created user pool
- Find the
App clientsitem in the menu on the left - Click
Create app client - Fill out the form as shown bellow:
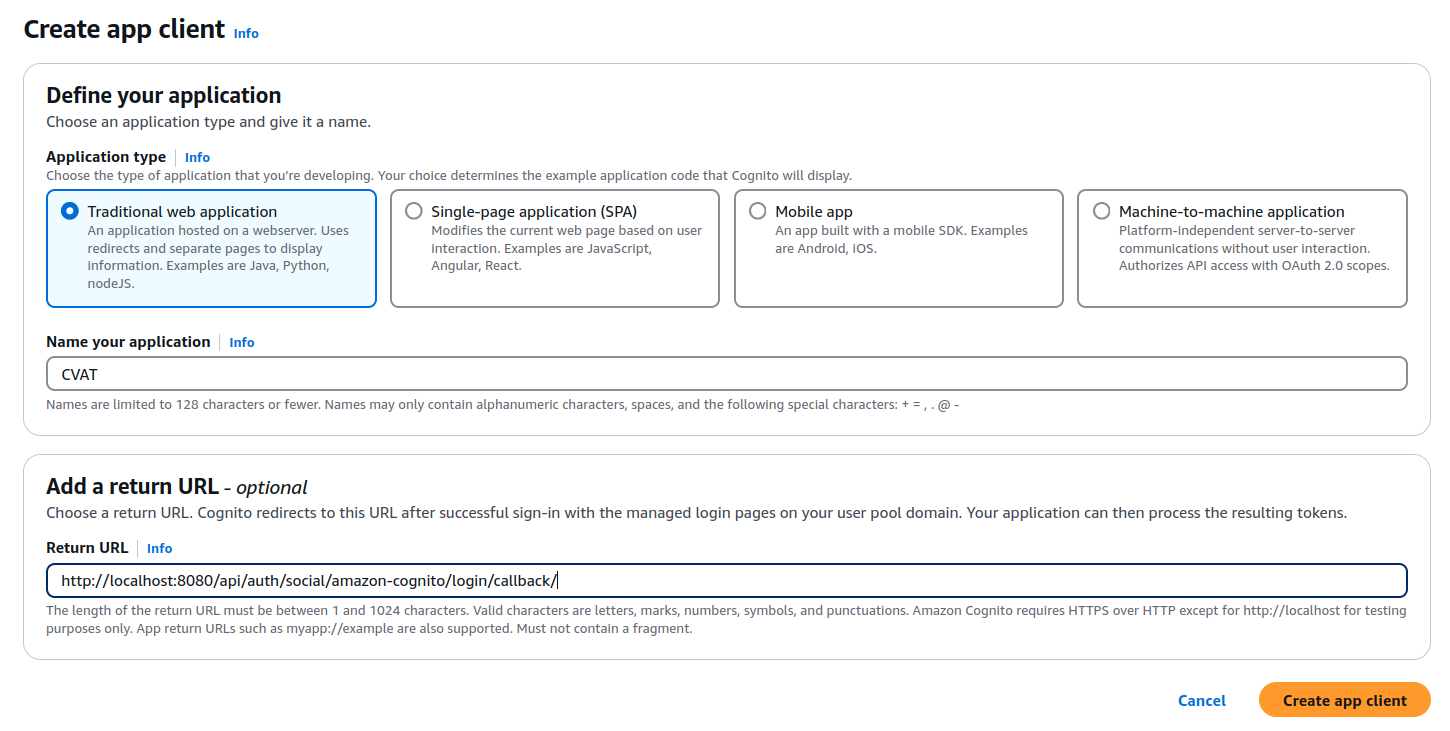
Application type:Traditional web applicationApplication name: Specify a desired name, or leave the autogenerated oneReturn URL(optional): Specify the CVAT redirect URL (<http|https>://<cvat_domain>/api/auth/social/amazon-cognito/login/callback/). This setting can also be updated or specified later after the app client is created.
- Navigate to the
Login pagestab of the created app client - Check the parameters in the
Managed login pages configurationsection and edit them if needed: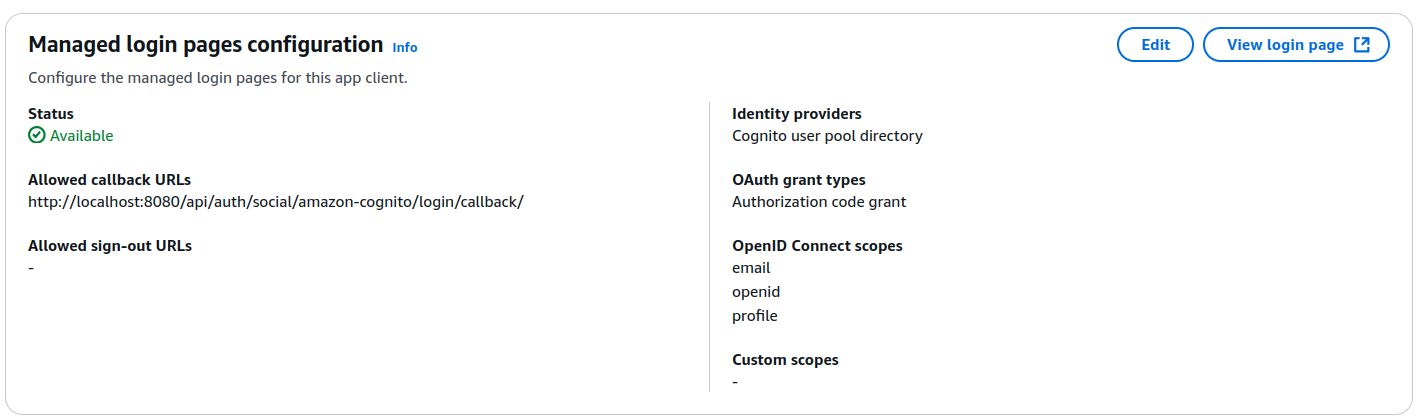
Allowed callback URLs: Must be set to the CVAT redirect URLIdentity providers: Must be specifiedOAuth grant types: TheAuthorization code grantmust be selectedOpenID Connect scopes:OpenID,Profile,Emailscopes must be selected
Setting up social authentication in CVAT
To configure social authentication in CVAT, create a configuration file
(auth_config.yml) with the following content:
---
social_account:
enabled: true
amazon_cognito:
client_id: <client_id>
client_secret: <client_secret>
domain: <custom-domain> or
https://<custom-cognito-prefix>.auth.us-east-1.amazoncognito.com
To find the client_id and client_secret values, navigate to the created app client page
and check the App client information section. To find domain, look for the Domain item in the list on the left.
Once the configuration file is updated, several environment variables must be exported before running CVAT:
export AUTH_CONFIG_PATH="<path_to_auth_config>"
export CVAT_HOST="<cvat_host>"
# cvat_port is optional
export CVAT_BASE_URL="<http|https>://${CVAT_HOST}:<cvat_port>"
Start the CVAT enterprise instance as usual.
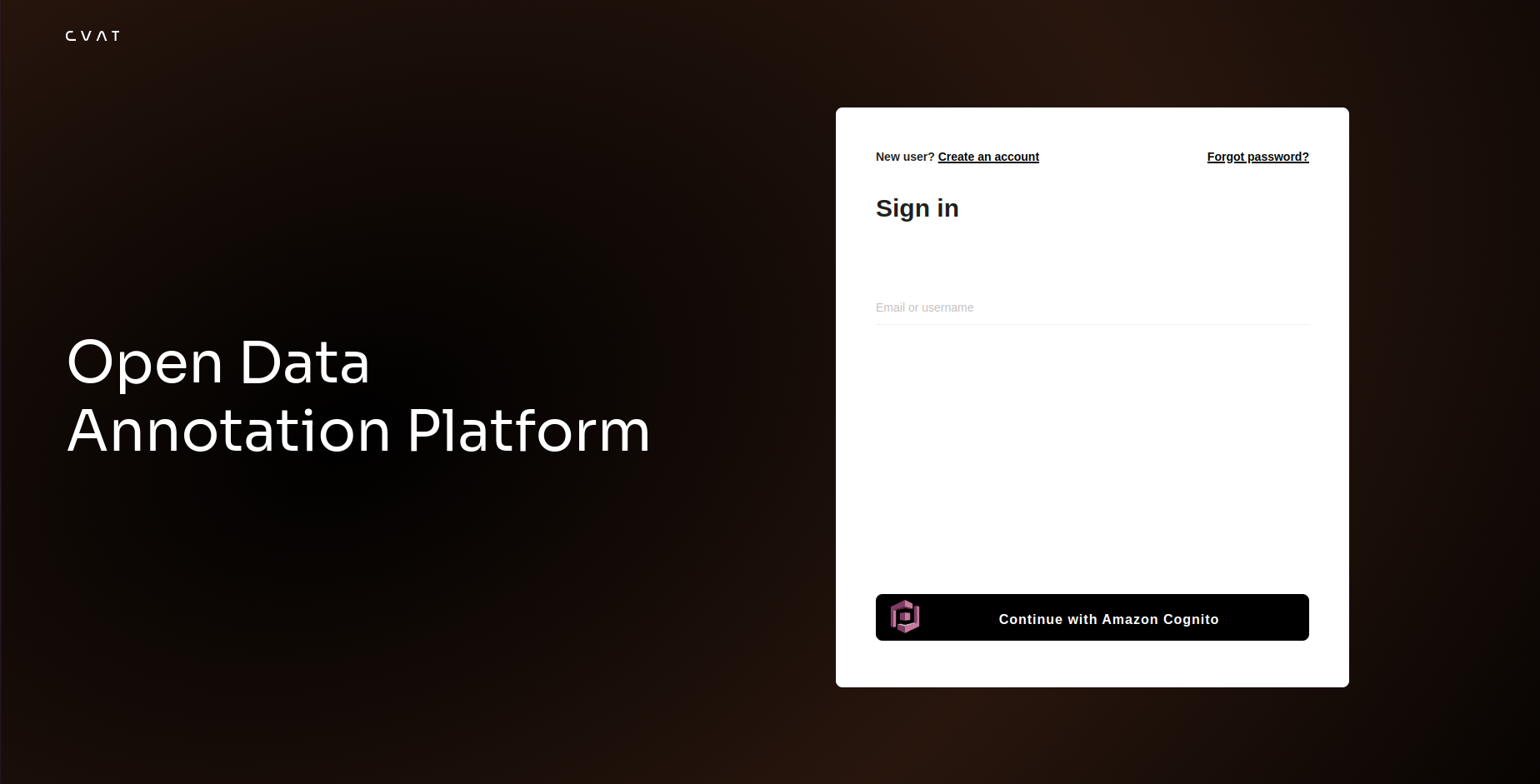
That’s it! On the CVAT login page, you should now see the option Continue with Amazon Cognito.